So, what are proxies ?
Proxy is a server that sits in between a client and an actual server. Word "proxy" defines, someone or something acting on behalf of something else. In computer science proxy means one server acting on behalf of other servers. A proxy server is a server (or computer system or an application) that acts as an intermediary for requests from clients seeking resources from other servers.
A client connects to the proxy server, requesting for some service (file, connection, web page) available from a different server and the proxy server evaluates the request as a way simplify and control its complexity. Proxies were invented to add structure and encapsulation to distributed systems.
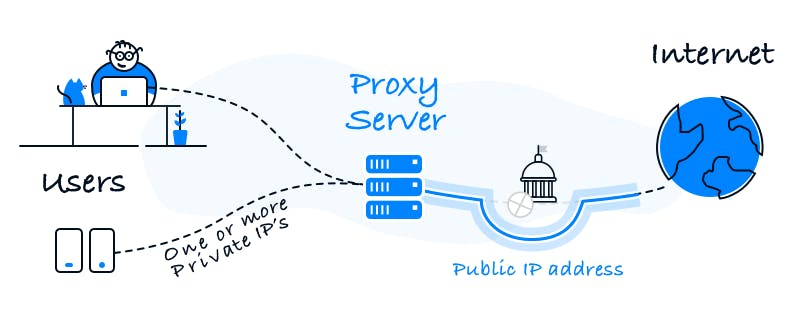
Without an online proxy, your device communicates directly with web servers. All the websites that communicate with your browser can see your device and speak with it directly. In other words, your IP address is public knowledge and exposed. But what if you want to get rid of all that public exposure? A web proxy or other proxy server sits in front of the client or a network of clients and handles this traffic on its behalf. This proxy server is another device that's connected to both the internet as well as your device, and it has its own IP address. Your device speaks only to the proxy server, and the proxy forwards all communication onward to the internet at large thus keeps the IP hidden at plain sight.
What does a proxy server do, exactly?
A proxy server plays many vital roles in managing the traffic and nodes across a network. Here's a few of the primary uses for a proxy server:
Firewalls: A firewall is a type of network security system that acts as a barrier between a network and the wider internet. Security professionals configure firewalls to block unwanted access to the networks they are trying to protect, often as an anti-malware or anti-hacking countermeasure. A proxy server between a trusted network and the internet is the perfect place to host a firewall designed to intercept and either approve or block incoming traffic before it reaches the network.
Content filters: Just as online proxies can regulate incoming connection requests with a firewall, they can also act as content filters by blocking undesired outgoing traffic. Companies may configure proxy servers as content filters to prevent employees from accessing the blocked websites while at work.
Bypassing content filters: That's right - you can outsmart a web proxy with another proxy. If your company's proxy has blocked your favorite website, but it hasn't blocked access to your personal proxy server or favorite web proxy, you can access your proxy and use it to reach the websites you want.
Caching: Caching refers to the temporary storage of frequently accessed data, which makes it easier and faster to access it again in the future. Internet proxies can cache websites so that they'll load faster than if you were to send your traffic all the way through the internet to the websites server. This reduces latency - the time it takes for data to travel through the internet.
Sharing internet connections: Businesses or even homes with a single internet connection can use a proxy server to funnel all their devices through that one connection. Using a Wi-Fi router and wireless-capable devices is another solution to this issue.
Wait - isn't that the same as a VPN?
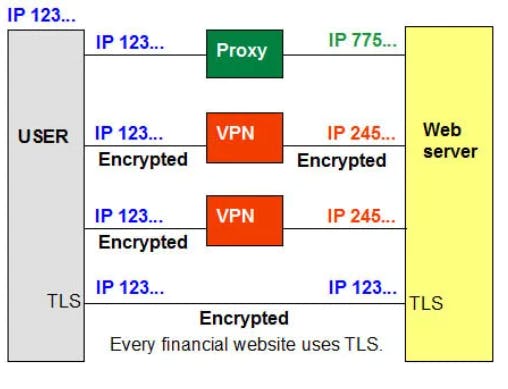
Proxies and VPNs both connect you to the internet via an intermediary server, but that's where the similarities end. While an online proxy simply forwards your traffic to its destination, a VPN encrypts all traffic between your device and the VPN server.
Types of Proxy Server
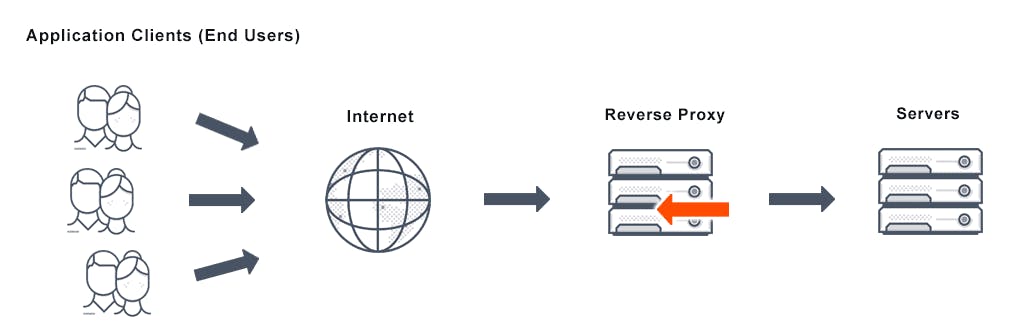
Reverse Proxy Server: The job of a reverse proxy server to listen to the request made by the client and redirect to the web server which is present on different servers.
Web Proxy Server: Web Proxy forwards the HTTP requests, only URL is passed instead of a path. The request is sent to particular the proxy server responds. Examples, Apache, HAP Proxy.
Anonymous Proxy Server: This type of proxy server does not make an original IP address instead these servers are detectable still provides rational anonymity to the client device.
Transparent Proxy: This type of proxy server is unable to provide any anonymity to the client, instead, the original IP address can be easily detected using this proxy. But it is put into use to act as a cache for the websites. A transparent proxy when combined with gateway results in a proxy server where the connection requests are sent by the client then, then IP are redirected. Redirection will occur without the client IP address configuration. HTTP headers present on the server-side can easily detect its redirection.
CGI Proxy: CGI proxy server developed to make the websites more accessible. It accepts the requests to target URLs using a web form and after processing its result will be returned to the web browser. It is less popular due to some privacy policies like VPNs, but it still receives a lot of requests also. Its usage got reduced due to excessive traffic that can be caused to the website after passing the local filtration and thus leads to damage to the organization.
Suffix Proxy: Suffix proxy server basically appends the name of the proxy to the URL. This type of proxy doesn't preserve any higher level of anonymity. It is used for bypassing the web filters. It is easy to use and can be easily implemented but is used less due to the more number or web filter present in it.
Tor Onion Proxy: This server aims at online anonymity to the user's personal information. It is used to route the traffic through various networks present worldwide to arise difficulty in tracking the users' address and prevent the attack of any anonymous activities. It makes it difficult for any person who is trying to track the original address. In this type of routing, the information is encrypted in a multi-fold's layer. At the destination, each layer is decrypted one by one to prevent the information to scramble and receive original content. This software is open-source and free of cost to use.
DNS Proxy: DNS proxy take requests in the form of DNS queries and forward them to the Domain server where it can also be cached, moreover flow of request can also be redirected and often hosted internally to an Organization.
Apart from the above types, the commonly used proxies are forward proxy server and reverse proxy server which are built to manage web services and client services on demand.
Forward Proxy Server:
A forward proxy is one who acts as a different requestor, so this proxy encapsulates the original identity of the requestor. Forward proxy can be used by the client to bypass restrictions in purpose to visit websites that are blocked by government, company or etc. Another usage of forward proxy is it can also act as a cache server. If the content is downloading multiple times, the proxy can cache the content on the server so when next time someone is downloading the same content, the proxy will send the content that is previously stored.
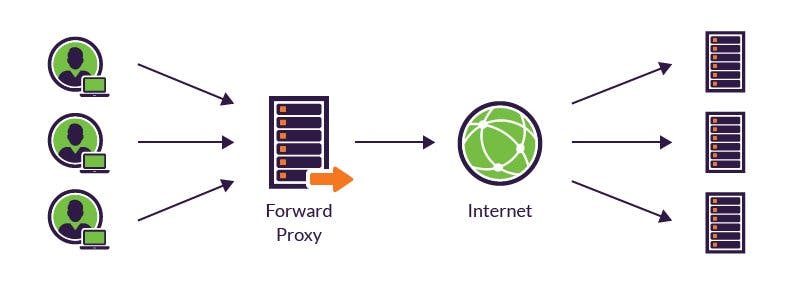
Reverse Proxy Server:
A proxy server is a go-between or intermediary server that forwards requests for content from multiple clients to different servers across the Internet. A reverse proxy server is a type of proxy server that typically sits behind the firewall in a private network and directs client requests to the appropriate backend server. A reverse proxy provides an additional level of abstraction and control to ensure the smooth flow of network traffic between clients and servers.
A reverse proxy operates by:
- Receiving a user connection request.
- Completing a TCP three-way handshake, terminating the initial connection.
- Connecting with the origin server and forwarding the original request.
Common use cases of Reverse Proxy scenarios:
There is a multitude of scenarios and use cases in which having a reverse proxy can make all the difference to the speed and security of your corporate network. By providing you with a point at which you can inspect traffic and route it to the appropriate server, or even transform the request, a reverse proxy can be used to achieve a variety of different goals.
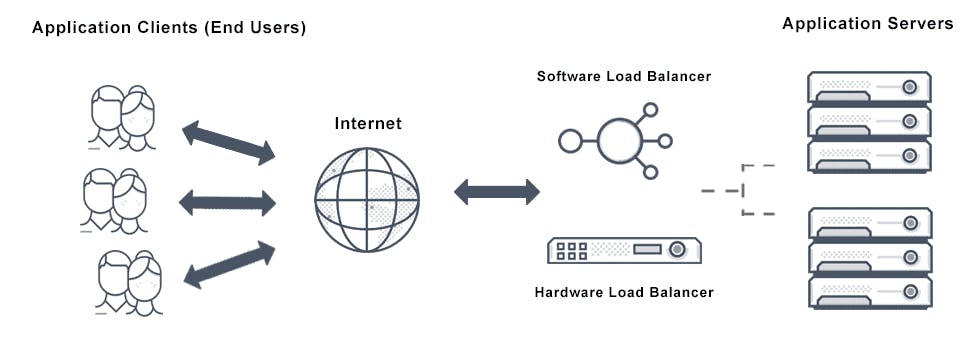
Load balancing: A reverse proxy server can act as a traffic cop that sits in front of your backend servers and distributes client requests across a group of servers in a manner that maximizes speed and capacity utilization while ensuring no server is overloaded, which can degrade performance. If a server goes down, the load balancer redirects traffic to the remaining online servers.
Web acceleration: Reverse proxies can compress inbound and outbound data, as well as cache commonly requested content, both of which speed up the flow of traffic between clients and servers. They can also perform additional tasks such as SSL encryption to take load off your web servers, thereby boosting their performance
Security and anonymity: By intercepting requests headed for your backend servers, a reverse proxy server protects their identities and acts as an additional defense against security attacks. It also ensures that multiple servers can be accessed from a single record locator or URL regardless of the structure of your local area network.
What are the Benefits of a Reverse Proxy Server?
Benefits of reverse proxy servers include:
- Load balancing
- Global server load balancing (GSLB)
- Caching content and web acceleration for improved performance
- More efficient and secure SSL encryption, and
- Protection from DoS attacks and related security issues.
Load balancing is the process of distributing network traffic across multiple servers. This ensures no single server bears too much demand. By spreading the work evenly, load balancing improves application responsiveness. It also increases availability bf applications and websites for users. Modern applications cannot run without load balancers
Reverse Proxy vs Forward Proxy
In contrast, a forward proxy server is also positioned at your network's edge but regulates outbound traffic according to preset policies in shared networks. Additionally, it disguises a client's IP address and blocks malicious incoming traffic.
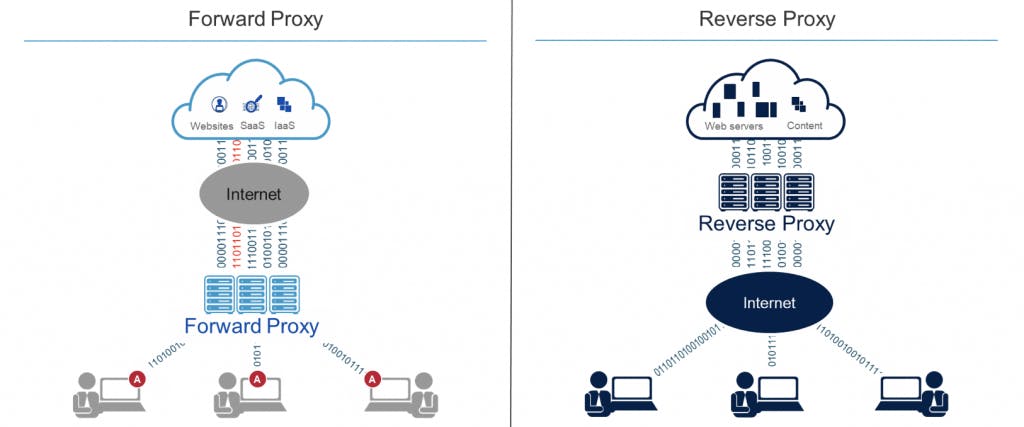
Forward proxies are typically used internally by large organizations, such as universities and enterprises to,
- Block employees from visiting certain websites.
- Monitor employee online activity.
- Block malicious traffic from reaching an origin server.
- Improve the user experience by caching external site content.
Benefits and Risks
Now that you know everything about proxies, here's a list of some of the benefits and risks associated with using them.
Benefits
- Secure and private internet browsing.
- Ability to get around geo-location restrictions.
- Better network performance.
- Ability to control what websites clients have access to.
- Many types to choose from to suit specific needs.
Risks
- Your requests might return really slow.
- Free or cheap proxies could be set up by hackers or government agencies.
- There are plenty more benefits and risks to using any of the proxy server types. That's why it is important to only connect to proxy servers you trust. When you are connected to a trusted proxy, the risks should have been taken into account in the configurations so you have less to worry about.
Proxy Server Risks: Free installation does not invest much in backend hardware or encryption. It will result in performance issues and potential data security issues. If you install a "free" proxy server, treat very carefully, some of those might steal your credit card numbers.
Browsing history log: The proxy server stores your original IP address and web request information is possibly unencrypted form and saved locally. Always check if your proxy server logs and saves that data - and what kind of retention or law enforcement cooperation policies they follow while saving data.
No encryption: No encryption means you are sending your requests as plain text. Anyone will be able to pull usernames and passwords and account information easily. Keep a check that proxy provides full encryption whenever you use it.
Conclusion:
Proxy and reverse proxy may sound similar but are different in terms of use cases and benefits. Both add the element of anonymity, proxy hides the identity of the client whereas the reverse proxy conceals the identity of the server. So, if you want to protect clients in your internal network, put them behind a forward proxy. On the other hand, if you intend to protect servers, put them behind a reverse proxy with proper firewall implementations enabled.